DID Actions
Here are the eleven (13) actions currently supported by DIDs as envisioned by Credentials Community Group and as intended in the DID Working Group Charter.
In the diagram, we have grouped the actions by Create, Read, Update, and Delete (CRUD) as well as Use.
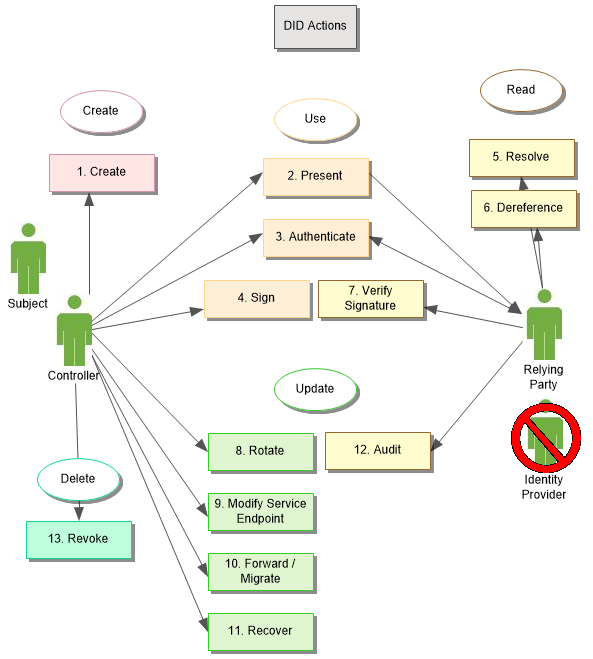
Create
Controllers create DIDs, uniquely binding cryptographic proofs with the identifier, typically using public-private key-pairs. These DIDs are recorded in a registry in such a manner as to be able to resolve to a DID Document. The DID Document may be dynamically and deterministically generated through resolution or it may be explicitly constructed as a stand-alone resource and either stored or referenced in the registry. This process needs access to the registry, ideally a decentralized system, and like the rest of the DID CRUD actions, can be performed without interaction with any particular authority.
Present
DIDs are URIs, which is to say a string of characters. As such, they may be presented in the same manner as URIs, by simply transmitting or presenting that string of characters. DIDs, however are not designed to be human readable. They invariably contain long, complex numbers represented in various formats. For ease of use, implementations often rely on QR codes for ease of capture using a camera-enabled device such as a smart phone.
Authenticate
Relying Parties may wish to prove that the individual presenting a DID is in fact its controller or specified as a Controller for a particular service endpoint. This authentication process uses the cryptographic material in the DID Document to test if the claimed Controller can, in fact, prove control, typically through some sort of challenge-response. Some DID Documents and methods allow for separate, proofs for different service endpoints, distinct from update and delete actions. This separation allows transactional proofs that are expected to be used frequently, while controlling proofs are used rarely.
Sign
Using cryptographic material associated with that found in a DID Document, DID Controllers may sign digital assets or documents. This signature can later be verified (#7 Signature Verification) to demonstrate the authenticity of the asset. In this way, we may referred to the asset as "signed by the DID".
Resolve
The first step in using a DID for anything other than presentation is to resolve the DID to a specific DID Document, to reveal the cryptographic material and service endpoints associated with that DID. How this occurs is method-specific and currently under development in the DID Resolution specification.
Dereference
Dereferencing a DID uses the material in its DID Document to return a resource. By default, dereferencing a DID without a reference to service endpoint returns the DID Document itself. When a DID contains a service name, dereferencing returns the resource pointed to from the named service endpoint, which was discovered by resolving the DID to its DID Document and looking up the endpoint by name. In this way, a Relying Party may dynamically discover and interact with the current service endpoints for a given DID.
Verify Signature
Given a digital asset signed by a DID, a Relying Party may use the cryptographic material in the DID Document to verify the signature.
Rotate
Controllers may rotate the cryptographic material for a DID by updating the DID Document as recorded in its registry. Different methods handle this differently, but the result is an update to the core cryptographic proof required to prove control of the DID and the DID Document.
Modify Service Endpoint
Controllers may change service endpoints associated with a DID, including the proof mechanism for authenticating as the Subject for any given endpoint. The process for doing this is method specific, but is designed to allow Controllers to make these change without necessarily changing the primary proof mechanism for control of the DID itself.
Forward / Migrate
To support interoperability, some methods provide a way for controllers to record in the registry (by updating the DID Document), that the DID should be redirected to another DID, which now has full authority to represent the originating DID. This mechanism allows DID controllers to migrate a DID from one method or registry to another.
Recover
Some methods provide means for recovering control of a DID if its existing private cryptographic material is lost. These means vary by method but can include social recovery, multi-sig, Shamir sharing, or pre-rotated keys. In general, recovery triggers a rotation to a new proof, allowing the Controller of that new proof to recover control of the DID without interacting with any Relying Parties.
Audit
Some methods provide an explicit audit trail of all CRUD actions on that DID, including a timestamp for when the actions took place. For distributed ledger-based registries, this audit trail is fundamental to the way the ledgers record transactions. This allows relying parties to see, for example, how recently a DID was rotated or its service endpoints updated, which may inform certain analytics regarding the reliability of the DID's cryptographic material.
Revoke
Instead of deleting a DID, Controllers can revoke a DID such that downstream processes like authentication and dereferencing are no longer functional. Most decentralized systems cannot guarantee actual deletion of a record. Indeed, distributed ledgers are often touted as "immutable". Methods define revocation processes to achieve the same effect as deletion. The mechanisms for revocation vary based on the method.